In Australia, several government agencies provide public-facing verification tools that allow individuals to confirm certain aspects of their records — such as enrolment status, registrations, or listings. These tools are designed primarily for citizens to check their own details quickly and conveniently.
However, an important policy question is emerging in practice:
How are public verification tools being used by third parties — including commercial investigators — and what are the permitted-use boundaries?
This article does not allege wrongdoing by any specific party. Instead, it highlights an area where public understanding and regulatory clarification would be beneficial.
Public Verification Tools: How They Work
Many government verification pages are intentionally accessible without account login. Typically, they allow a result to be displayed when certain matching personal fields are entered — for example:
name
date of birth
locality or address components
The output usually confirms limited status information rather than exposing full records. These tools are designed for convenience and transparency.
From a technical standpoint, these are verification interfaces, not private dashboards or authenticated personal portals.
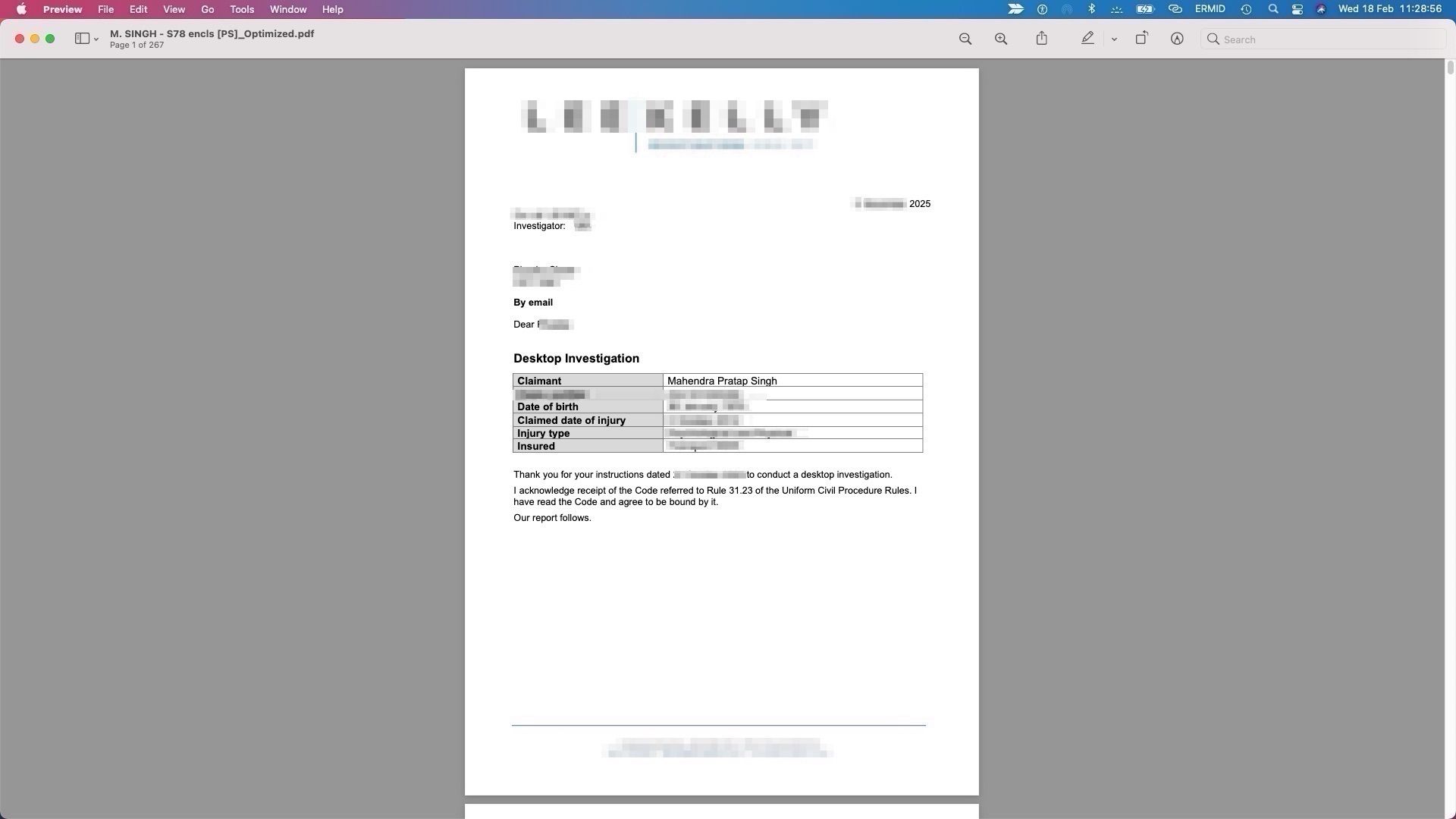
A Practical Reality: Third-Party Use in Investigations
In civil and insurance contexts, commercial desktop investigations are commonly performed. These investigations often include:
open-source intelligence (OSINT)
public record checks
social media review
business registry searches
publicly available verification tools
In some cases, verification results from public government lookup pages may be captured as screenshots and included in paid investigation reports prepared for legal or insurance purposes.
This raises a reasonable governance question:
When a public verification page is designed for personal self-check, is third-party commercial capture and reuse of that output within intended use — or does it sit in a grey policy zone?
Why This Matters for Citizens
Most members of the public assume:
if a government page shows their data,
and no login is required,
then the tool is meant for self-verification only.
But in practice, if matching personal details are known, the same interface may be used by others to confirm status and generate a visual record of the result.
Even when lawful, this can feel surprising to individuals who were unaware such reuse occurs in commercial reporting contexts.
Awareness — not alarm — is the goal here.
Key Distinctions That Should Be Kept Clear
It is important to distinguish between:
Permitted
accessing publicly available verification tools
confirming status fields
recording publicly displayed outputs
Not permitted
hacking protected systems
bypassing authentication controls
accessing restricted databases
impersonating identity to enter private portals
Public verification interfaces are fundamentally different from secure account dashboards — and discussion should keep that distinction precise.
The Policy Question Going Forward
This is ultimately a policy clarity issue, not an accusation issue.
Reasonable questions regulators may wish to address include:
Are public verification tools intended for third-party commercial investigation use?
Are there recommended limits on screenshot reuse in paid reports?
Should terms of use more explicitly address commercial capture?
Should citizens be more clearly informed about possible third-party lookup scenarios?
Are additional safeguards or usage guidance appropriate?
Clear guidance benefits everyone:
citizens, investigators, insurers, and regulators alike.
A Call for Clarification, Not Confrontation
As digital verification tools expand, clarity around intended use vs practical use becomes increasingly important.
The goal is not to restrict transparency tools — but to ensure:
expectations are aligned
permitted uses are defined
safeguards are understood
public trust is maintained
Constructive regulatory clarification is the healthiest path forward.